#KEYMASTER: PKI-Powered Code Signing for the CI/CD Era
2026-02-19
In this #KEYMASTER episode, Ben Dewberry, Product Manager, Signing and Key Management, joins Sven Rajala to discuss the status of code signing in Enterprises.
Enterprise signing has quietly but fundamentally changed. Not long ago, signing was often treated as a secondary concern, with ad hoc solutions implemented to meet immediate requirements. A developer or release engineer would log into a workstation, use a locally stored key file, and manually sign an MSI, DLL, JAR, or similar artifact before moving on. The objective was straightforward: ensure the file was signed so it could be distributed. Today, that model no longer holds.
Modern enterprises build and ship software through automated CI/CD pipelines. Signing is no longer a manual, one-off activity, it is a critical control point embedded deep into development workflows. Artifacts are signed automatically as part of pipeline stages, often without human intervention. This shift has raised the bar from how do I sign a file to how do I design signing as part of a secure, scalable delivery system.
From Files to Pipelines and Containers
As CI/CD pipelines became the norm, software packaging evolved alongside them. Applications are no longer delivered as standalone binaries alone. They are bundled into container images, deployed into Kubernetes clusters, and promoted across environments at high velocity. That changes the signing problem.
Enterprises now need to sign:
- Application artifacts (binaries, libraries, packages)
- Container images themselves
- Associated metadata such as SBOMs and attestations
And just as importantly, they need to verify all of it before anything runs in production.
This is where container signing has seen rapid movement. The ecosystem has largely converged around Cosign, part of the Sigstore project under the Linux Foundation. Cosign introduced a modern, developer-friendly approach to signing container images, backed by transparency logs and short-lived identities. With Docker stepping away from Notary, Cosign has become the dominant model for container signing in practice.
Open Source Meets Enterprise Reality
Sigstore’s public trust model works well for open source and community-driven projects. But enterprise environments bring additional constraints.
Many organizations already operate a private PKI that underpins their internal trust model, issuing certificates for workloads, services, and users. When those same organizations deploy software internally, they often want:
- Signing identities rooted in their existing private PKI
- Long-lived or policy-controlled signing keys
- Hardware-backed key protection using HSMs
- Clear auditability and separation of duties
Rather than replacing Sigstore-style workflows, enterprises increasingly want to integrate them with their own trust infrastructure. This is where enterprise signing platforms can bridge the gap, supporting Cosign-compatible workflows while keeping private keys protected, managed, and compliant with internal security requirements.
End-to-End Supply Chain Control
The real power of modern signing emerges when everything is connected.
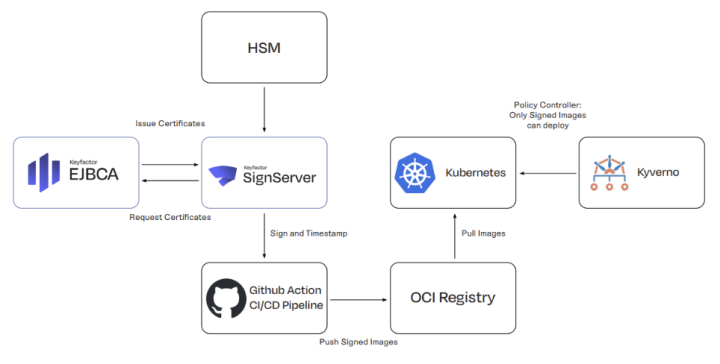
A mature pipeline can:
- Build an application
- Sign and timestamp the application artifact
- Verify app and package it into a container
- Sign and timestamp the container image
- Generate and sign an SBOM or attestation
- Store everything together in a registry
- Verify Image signature with Kyverno before deployment
Securing the CI/CD Supply Chain with Trusted Signatures
With Kubernetes policy engines, organizations can enforce rules such as: if this image wasn’t signed by our trusted PKI, it doesn’t run. This turns signing from a compliance checkbox into an active security control across the entire software supply chain.
Short-Lived Keys, Mixed Trust Models, and Flexibility
Enterprises are also experimenting with different signing models:
- Public trust for software distributed externally
- Private trust for internal deployments
- Hardware-backed keys for high-value signing operations
- Ephemeral, short-lived certificates for automated pipelines
The reality is not one-size-fits-all. Most organizations end up with a hybrid approach, balancing security, automation, and operational complexity.
Looking Ahead: Post-Quantum Signing
Interest in post-quantum cryptography (PQC) is no longer theoretical, especially in regulated industries and IoT-heavy environments.
While many native signing tools are still catching up, there is growing demand for:
- Post-quantum and hybrid signatures
- PQC-safe timestamping
- Control over signature formats (such as CMS) while standards mature
For many teams, this work starts in labs and pilots today, with an eye toward future-proofing signing workflows before standards and mandates fully land.
Key Takeaways:
- Signing has shifted from manual tasks to automated pipeline controls.
If signing isn’t integrated into CI/CD, it’s already lagging behind. - Containers changed the scope of signing.
It’s no longer just about binaries; it’s about images, metadata, and attestations. - Cosign is now the dominant container signing tool, but enterprises need flexibility.
Many want Sigstore-style workflows backed by private PKI and HSMs. - End-to-end verification is the real goal.
Signing only matters when verification is enforced at deployment time. - Hybrid trust models are the norm.
Public, private, long-lived, and short-lived signing identities all coexist. - Post-quantum signing is moving from “future” to “planning now.”
Especially for IoT and long-lived assets, PQC readiness is becoming a real requirement.
Enterprise signing is not just about cryptography anymore; it’s about designing trust into how software is built, shipped, and run.
Learn more
Related resources

#KEYMASTER: Why PKI Matters for the Matter IoT Standard
